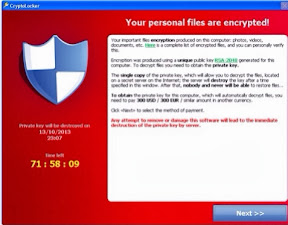
There is a new pest for InfoSec to fight and it is called Ransomware. Though not new, it has become far more invasive and destructive to anyone that has experienced it.
The success of CryptoLocker has spawned new variants (Prison Locker Power Locker, etc..) that will further spread the terror to companies, people, government agencies, police departments and anyone else. It will only get worse as CryptoLocker proved there is SERIOUS money to be made with this type of attack.
So what do we do? How do we defend against it? How do we detect such annoying and destructive attacks? How do we know which directories and data to restore?
Anyone who hears my presentations and soapbox statements and discussions, I feel Prevention is a dead idea. If you still think you can prevent all this hacker stuff, think again. They have proved over and over again that the Bad Actors win and the Good Actors lose with there tails between their legs in defeat or worse, fired. Just ask Target, Neiman Marcus, or the other 6 others yet to be named retailers that have also fallen to the Black PoS hack.
CryptoLocker now has 3 known variants and was re-written from C++ to C# to improve the tool. This is bad news for InfoSec Blue Teamer's like myself. We must evolve faster and quicker than the malwarians update, morph or create new variants.
Or do we?
I am an advocate of Detect and Respond and less on Compliance and Prevention. I personally believe Compliance is why the hackers are winning and making a fortune. We chase compliance audits, the paperwork, the check boxes and in the process fail to do Real Security. You can't prevent invention, it's the mother of necessity and can't stop clever people trying to compromise your systems, unless of course you just disconnect from the Internet...
I often tell people, if you are not logging everything, you are doing it wrong.
So how do you deal with this type of destructive malware attack? You can block email attachments, but that won't stop them as they offer up scripting on compromised websites that will execute the script to call the loader to download and install the malware via the browser.
So what do we do?
Detect and Response is the only answer! You can detect a CryptoLocker type event pretty easily actually, but few actually practice this particular type of defense. 'Times are a changin' and so should you, so here is how you can detect a CryptoLocker type attack.
Logging to the rescue - View of a typical CryptoLocker event. Notice how quiet it is to the left of the event.
Step 1 - Force Advanced Auditing
The first thing you must do is force your clients to use the new Advanced Auditing features of Windows Vista, Windows Server 2008 or later operating systems. You will find this setting under Security Options on your local system or Group Policy. Don't worry, for older XP and Server 2003 and earlier systems, the older auditing works fine for this event.Once you have enabled this setting, you now can set the new Advanced Audit Policies in Windows Vista, Server 2008 or later operating systems.
Step 2- Enable Object Access - File System to SUCCESS
You will only need success for this setting as you want to know which files were changed, not that failed.
This will now enable Event ID = 4663 which will add an event in the Security Log anytime a file is deleted or written to.
Now you have to decide what directories you are going to audit this for. Unfortunately this must be enabled on every parent directory you want to monitor on the local system, manually or by scripts. Sorry no GPO for this that I am aware of. This means every users "My Documents" folder, data drives or file server shares. This is a local system setting (on the actual computer) so you will need to visit each system remotely or in person, or use an automated way to enable File Auditing for specific directories.
Step 3 - Enable File Auditing for a directory you want/need to monitor.
On the local system you will navigate to the parent directory and add auditing. Here is how to do it manually:1. Select a folder
2. Right-Click - Select PROPERTIES - SECURITY - ADVANCED - AUDITING tab
3. Edit - ADD - EVERYONE - OK
It will bring you to the following screen:
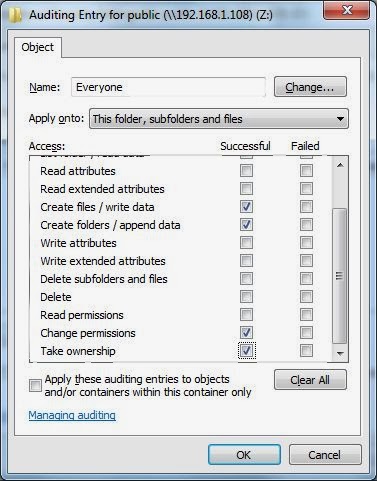
4. Select - "This folder, subfolders and files" (the default)
5. Check - Create files / write data
6. Check - Create folders / append data
7. Check - Change permissions
8. Check - Take ownership
* deselect everything else unless you have already set something and need it
When you select "OK" and apply, it will grind through all the folders and files enabling the file auditing. This places minimal burden on the file server with today's systems, but by all means test it yourself.
Now when a CryptoLocker type event occurs your logs will capture the event. If you are using a Logging solution like Splunk (my personal and professional recommendation) you can see the events and setup alerts to trigger when a threshold outside the norm of your users is reached. I suggest "> 250 events per hour" as a place to start and adjust accordingly to your unique environment.
From the graph above and the view below you can see 3600+ events occurred and in my case an email and SMS message alerted me to the event allowing me to take immediate action.
In addition, the results can tell you what user (WHO) and what system (WHERE) along with all the files (WHAT) that were affected and therefor what to restore.
Blue Team Defender doesn't get any better than this!
Try it out on a test system and use Splunk's FREE Splunk Storm cloud offering to tweak you results and get to know Splunk.
This detector also works for any current or disgruntled employee that mass deletes or changes files. Once you enable auditing on servers with large amounts of data and lots of users that can access and potentially alter it, a CryptoLocker type event can cripple your organization or at a minimum create a minor to serious outage.
SPLUNK OUT !
#InfoSec #HackerHurricane #Splunk #CryptoLocker




